RPADACertificateRenewal
This program automates a complex certificate renewal process in the Kofax RPA system, reducing human error and saving many hours of downtime.
Problem
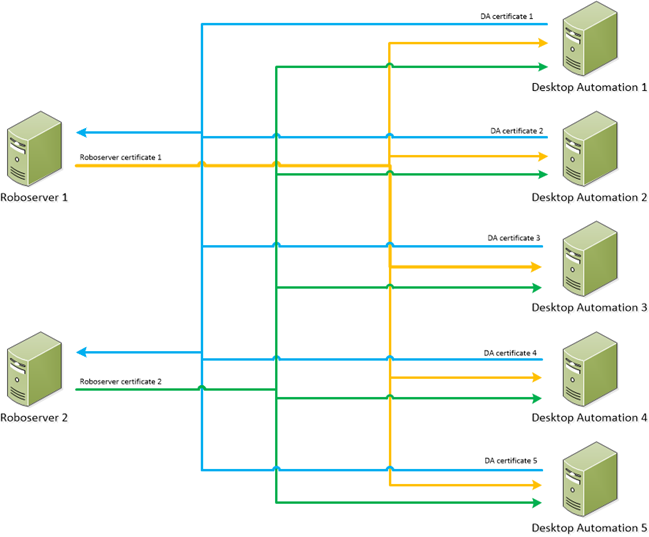
While Kofax RPA does use certificates for various connections between servers, these certificates are not unique to us as a customer, so we considered this a security risk. To mitigate this risk, I generated unique self-signed certificates, however this led to a complex renewal process with plenty of room for human error, and often took several attempts before the RPA system could be brought back online. To highlight the complexity of this task, here’s a diagram of just one set of certificates:
Solution
I automated the renewal process by developing RPADACertificateRenewal, which automatically generates and deploys new certificates for every server/service, and restarts the RPA system.
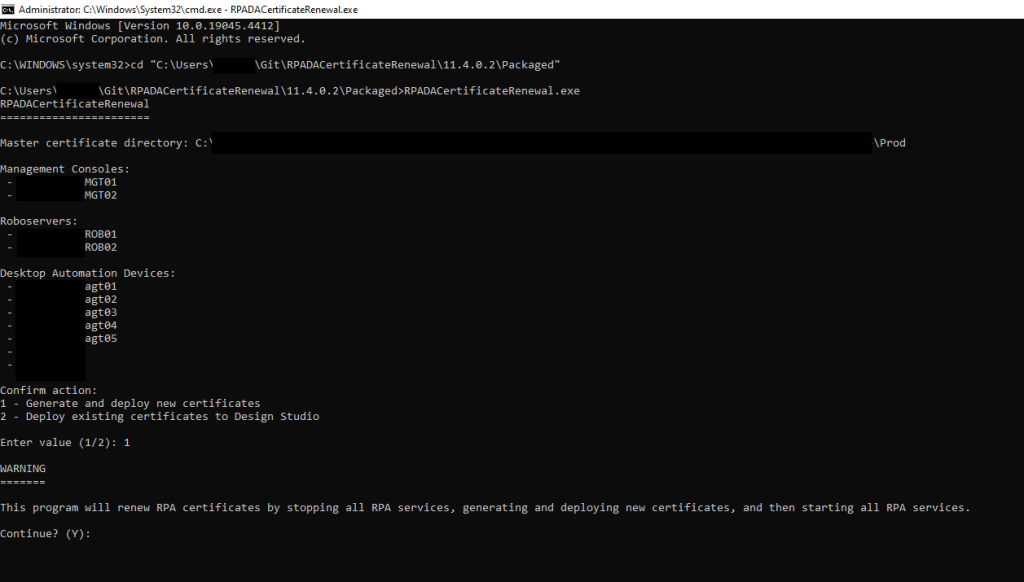
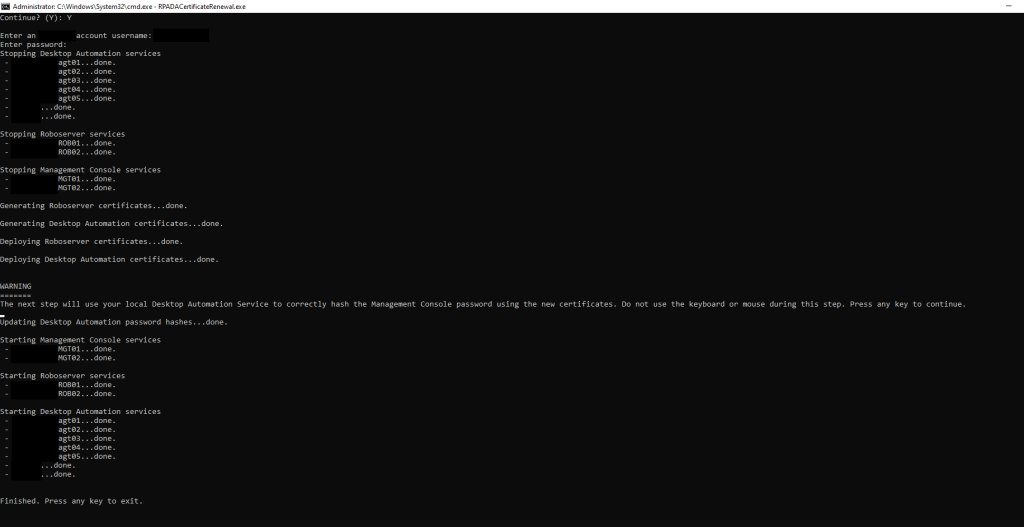
Technologies
I used several technologies to develop this service:
Microsoft .NET Framework / C#
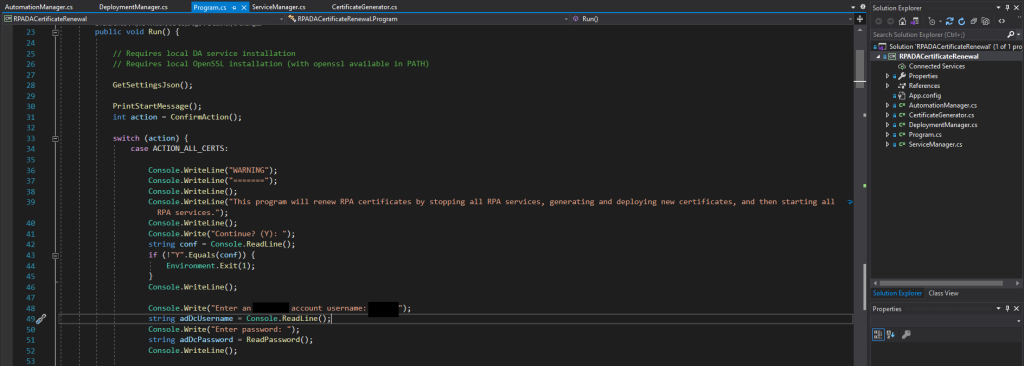
I used the Microsoft .NET Framework to develop a console application written in C#.
OpenSSL
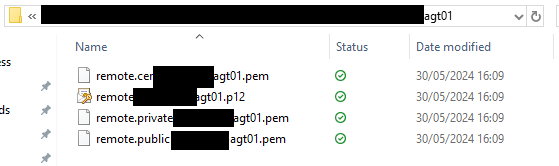
Because RPA expects certificates in the pem format, I used OpenSSL to convert PKCS #12 certificates into public/private pem certificates.
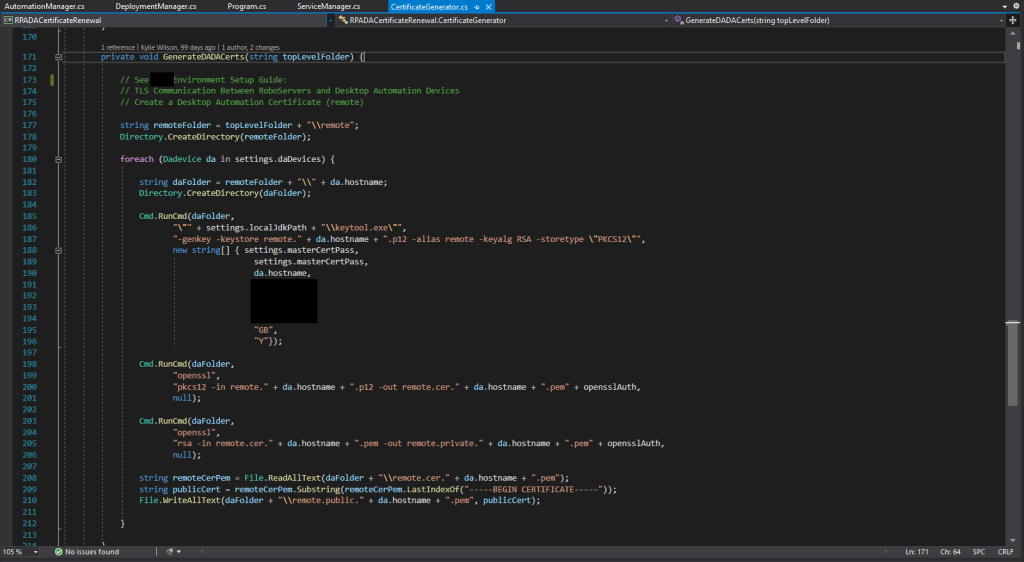
Java
I used the Java keytool to generate PKCS #12 certificates.
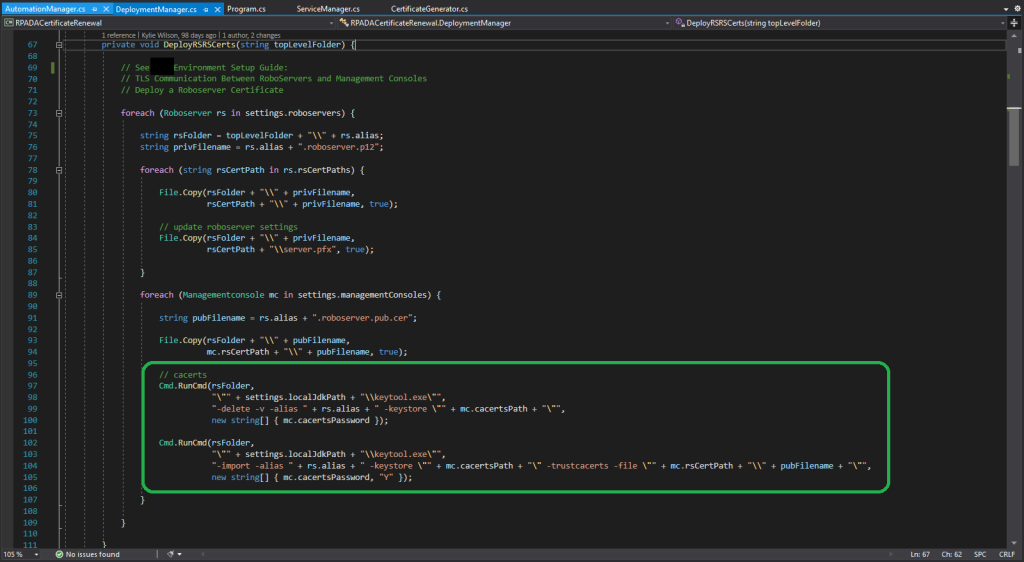
Some certificates also need to be automatically added to the Java cacerts keystore on certain RPA servers:
JSON
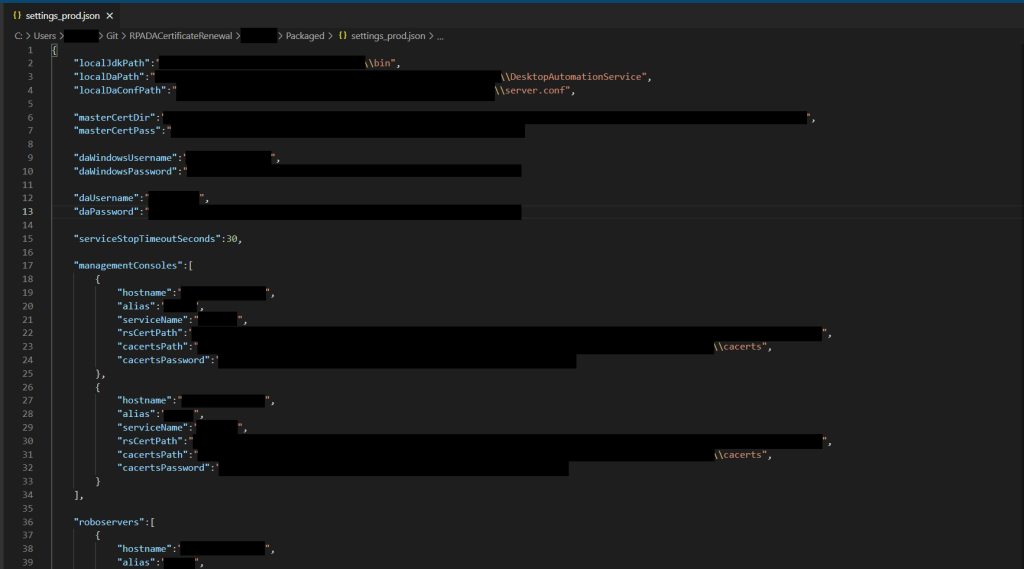
Program settings are stored in a JSON file:
Challenges
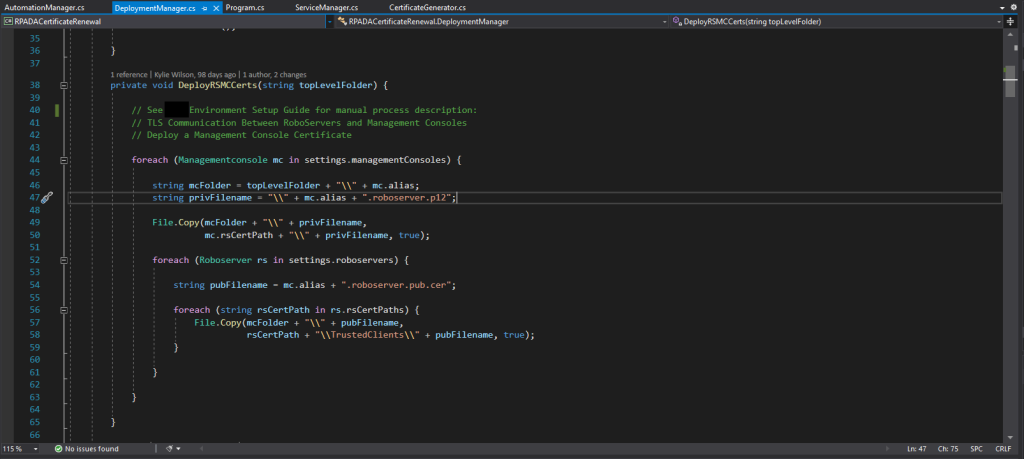
Given the complexity of the manual renewal process, automating this task was quite a technical challenge, involving several nested for loops iterating over RPA servers/services, and deploying public/private keys to ensure that each relationship is unique:
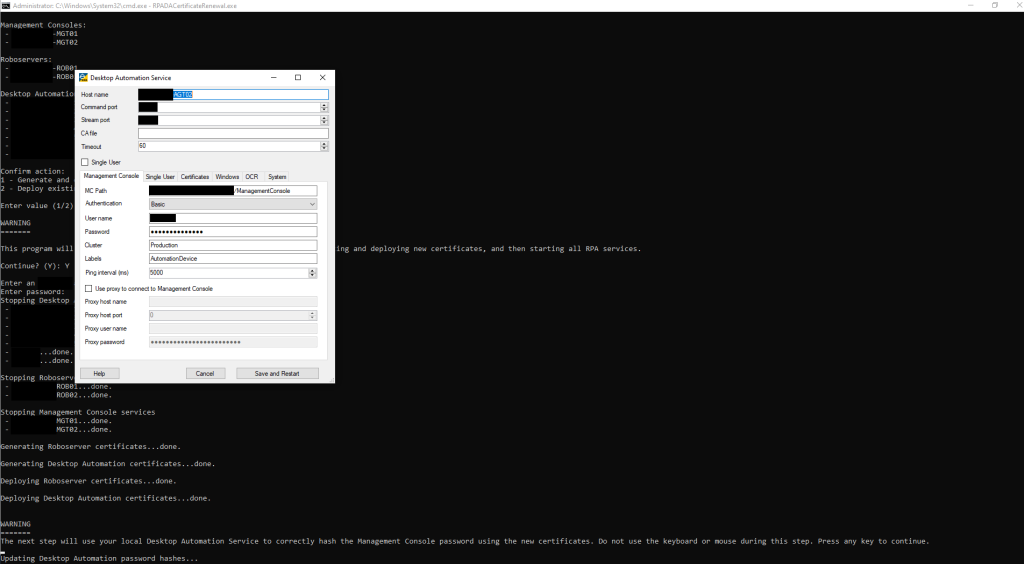
I also faced a challenge where a certificate could only be deployed via a front-end GUI, meaning that automating this would be difficult without developing an RPA robot for this task. More specifically, I found that the Desktop Automation Service hashes a password against a certificate using an unknown algorithm, meaning that settings had to be manually saved again so that the password was re-hashed by the service itself. To work around this, I used the Microsoft UI Automation library to automate the GUI of a local instance of the Desktop Automation Service, then copied the local files containing the new password hash onto the appropriate server:

Leave a Reply